Introduction
🔥 “Namaste Bhaiyo and Behno!”
So in this blog, we’re going to learn everything about Nmap —
👉 What it is
👉 Why we use it
👉 How it works
But wait… we won’t just learn it — we’ll actually understand it deeply and use it like real hackers with full hacker energy! 😎💻
So, are you ready to network scanning with Nmap and uncover the digital world like a pro?
Let’s dive in! 🔍💥
WHAT IS NMAP
English:
Nmap (Network Mapper) is a powerful open-source network scanning tool used to discover hosts and services on a computer network. It’s the Swiss Army knife for network admins and ethical hackers.
Hindi:
Nmap ek powerful open-source network scanning tool hai jo kisi bhi network mein devices aur services ko detect karne ke liye use hota hai. Ye tool network admins aur ethical hackers ke liye ek Swiss Army knife jaisa kaam karta hai.
🔹 Why we use network scanning with Nmap
English:
We use Nmap to:
- Discover active devices (hosts) on the network
- Identify open ports and running services
- Perform OS detection, version detection, and vulnerability scanning
- Map network structure and find security loopholes
Hindi:
Nmap ka use isliye karte hain:
- Network mein active devices ko dhoondhne ke liye
- Open ports aur unpe chal rahi services ko identify karne ke liye
- OS aur version detect karne ke liye
- Network structure samajhne aur vulnerabilities dhoondhne ke liye
🔹 How Nmap works (network Scanning Process)
English:
Nmap sends different types of packets (like TCP, UDP, ICMP) to the target and analyzes the responses. Based on reply/no reply, it detects:
- Is the system alive?
- Which ports are open?
- What OS/services are running?
It can even bypass firewalls using stealth scans and run advanced scripts for deep scanning.
Hindi:
Nmap alag-alag tarah ke packets bhejta hai (jaise TCP, UDP, ICMP) bhejta hai aur unka response analyze karta hai. Reply aata hai ya nahi, uske basis par:
- System zinda hai ya nahi
- Kaunse ports open hain
- Kaunsa OS aur service chal rahi hai
- Ye tool firewalls ko bypass bhi kar sakta hai aur ascripts run karke deep scanning bhi karta hai.
How to Install Nmap
🔹 Windows:
- Go to: https://nmap.org/download.html
- Download the Windows Installer and install like normal software.
🔹 Linux (Ubuntu/Kali):
sudo apt update
sudo apt install nmap
🔹 Termux (Android):
pkg update
pkg install nmap
⚙️ How to Use and Setup Nmap
- Run Nmap from Terminal (Linux/Termux) or CMD (Windows)
- Syntax : nmap [options] <target>
-
Examples:
- Single IP: nmap 192.168.1.1
- Range: nmap 192.168.1.1-50
- Subnet: nmap 192.168.1.0/24
- Hostname: nmap scanme.nmap.org
Nmap Commands Explained
1. Ping Scan : -sn
- Command : nmap -sn <target>
- -sn: Ping scan only, no port scan.
- English: Checks if the host is up without scanning ports.
- Hindi: Host zinda hai ya nahi yeh check karta hai, ports scan nahi karta.
2. ARP Ping Scan : -sn -PR
- Command: nmap -sn -PR <target>
- -PR: Sends ARP packets.
- English: Detects live hosts on LAN using ARP packets.
- Hindi: LAN me active devices dhoondhne ke liye ARP ka use karta hai.
3. UDP Ping Scan : -sn -PU
- Command: nmap -sn -PU <target>
- -PU: Sends UDP packets.
- English: Checks if the host is up using UDP packets.
- Hindi: UDP ke through ping karke system ke alive hone ka pata lagata hai.
4. ICMP Echo Ping Scan : sn -PE
- Command: nmap -sn -PE <target>
- -PE: ICMP echo request.
- English: Sends a standard ICMP ping to check host availability.
- Hindi: Normal ping ke through system zinda hai ya nahi, yeh dekhta hai.
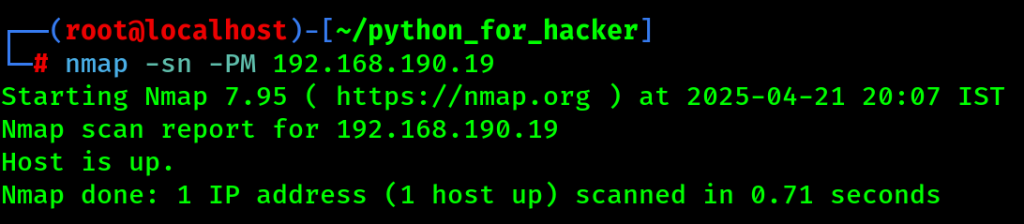
5. ICMP Address Mask Ping Scan : -sn -PM
- Command: nmap -sn -PM <target>
- -PM: ICMP address mask request.
- English: Sends address mask requests to determine subnet info.
- Hindi: Subnet mask info lene ke liye ICMP packet bhejta hai.
6. TCP SYN Ping Scan : -sn -PS
- Command: nmap -sn -PS <target>
- -PS: Sends TCP SYN packets.
- English: Sends SYN packets to find live hosts.
- Hindi: TCP SYN packet bhej ke host active hai ya nahi, yeh detect karta hai.
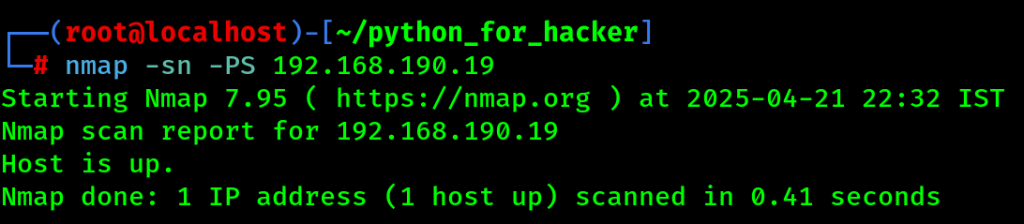
7. TCP ACK Ping Scan : sn -PA
- Command: nmap -sn -PA <target>
- -PA: Sends TCP ACK packets.
- English: Uses ACK packets to discover hosts behind firewalls.
- Hindi: Firewalls ke peeche hosts dhoondhne ke liye ACK packet use karta hai.
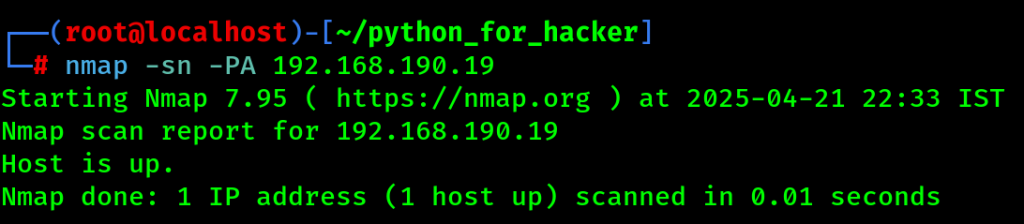
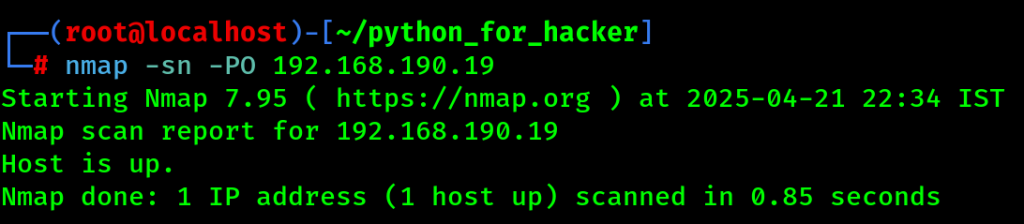
8. IP Protocol Ping Scan : sn -PO
- Command: nmap -sn -PO <target>
- -PO: Sends IP protocol packets.
- English: Detects live hosts using various IP protocols.
- Hindi: IP protocol ke alag-alag packets se check karta hai host online hai ya nahi.
9. TCP Connect Scan : sT -v
- Command : nmap -sT -v <target>
- -sT: TCP full connect scan.
- -v: Verbose mode.
- English: Establishes full connection to scan ports.
- Hindi: Full 3-way TCP handshake ke saath ports scan karta hai.
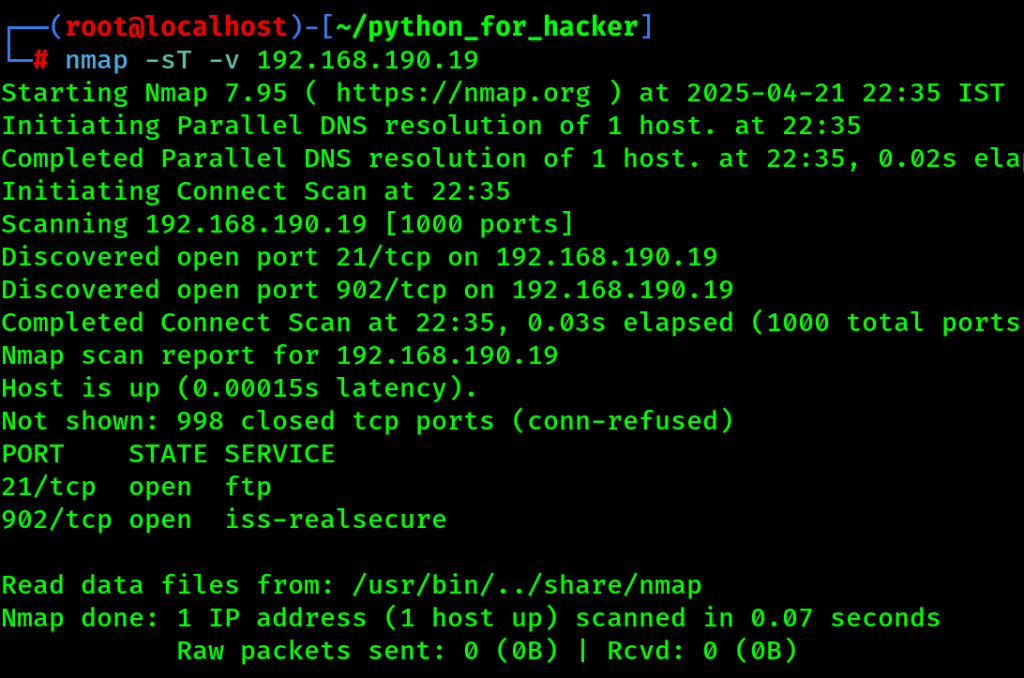
10. Stealth SYN Scan : -sS -v
- Command: nmap -sS -v <target>
- -sS: Half-open (stealth) scan.
- English: Sends SYN and waits for reply, no full connection.
- Hindi: Sirf SYN bhejta hai, full handshake nahi karta (stealth).
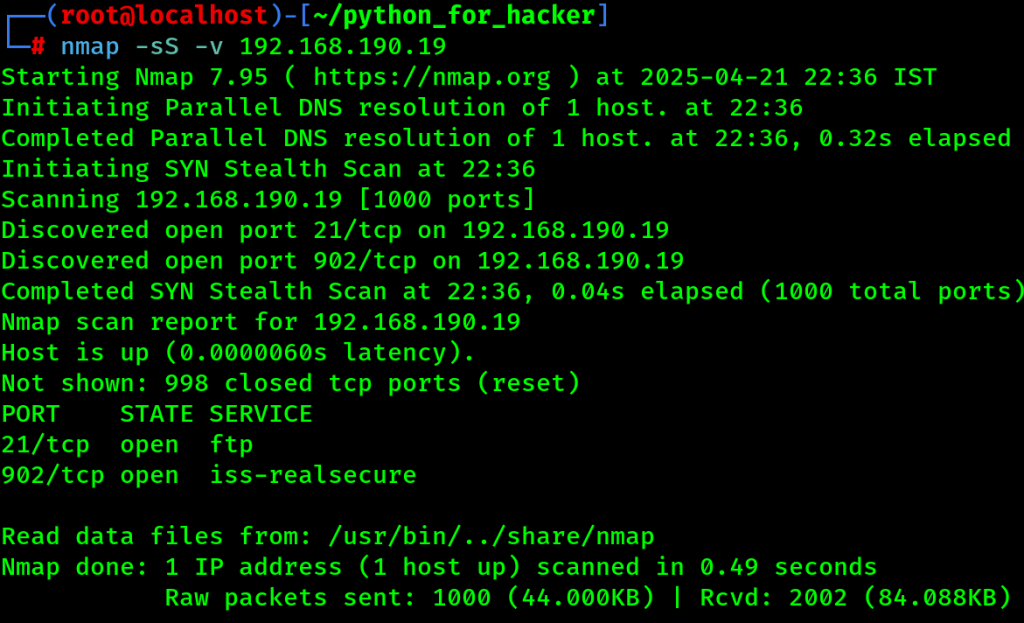
11. Xmas Scan : -sX -v
- Command: nmap -sX -v <target>
- -sX: Sends packets with FIN, URG, PSH flags.
- English: Attempts to bypass firewalls using Xmas packets.
- Hindi: TCP ke special flags ke saath scan karta hai (firewall confuse karne ke liye).
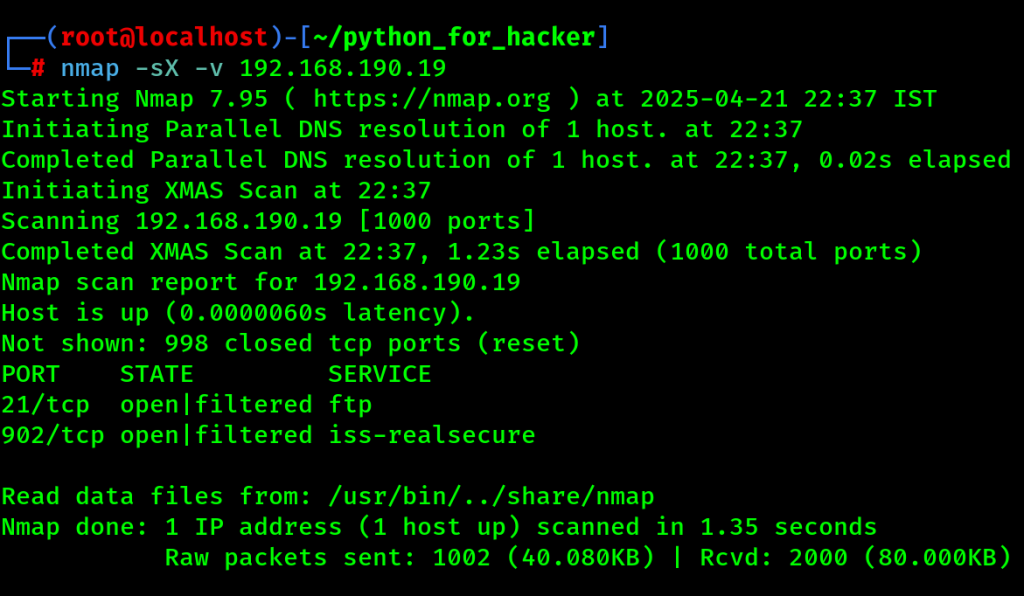
12. ACK Scan : -sA -v
- Command: nmap -sA -v <target>
- -sA: Sends TCP ACK packets.
- English: Used to map firewall rules.
- Hindi: Firewall ke rules ka pata lagane ke liye use hota hai.
13. UDP Scan : -sU -v
- Command: nmap -sU -v <target>
- -sU: UDP port scan.
- English: Scans UDP ports for open services.
- Hindi: UDP ke ports pe check karta hai services run ho rahi hain ya nahi.
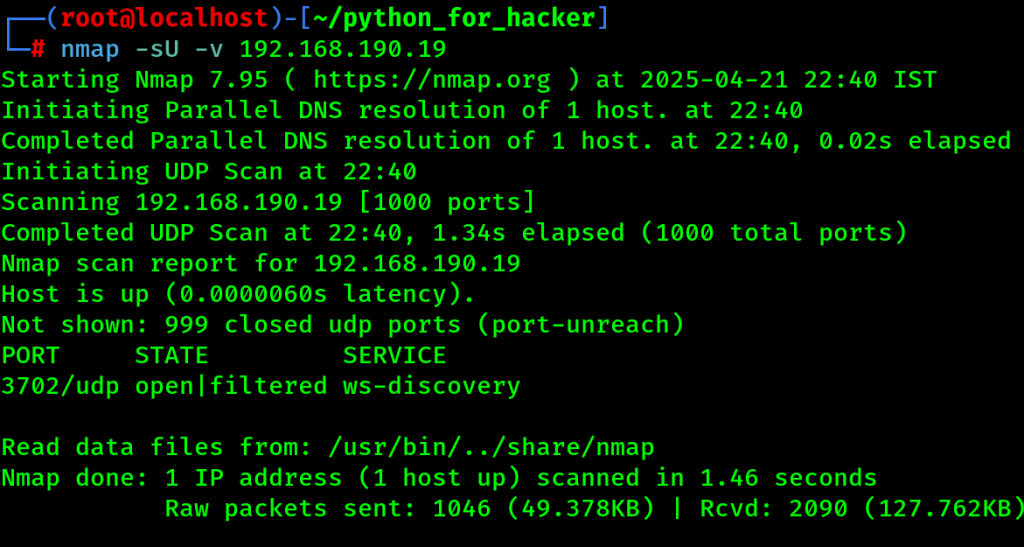
14. Aggressive Full Scan : -T4 -A -v
- Command: nmap -T4 -A -v <target>
- -T4: Timing template (fast).
- -A: Enables OS, version, script & traceroute.
- English: Fast and detailed scan.
- Hindi: Jaldi aur detailed scanning karta hai (OS, services, versions, etc).
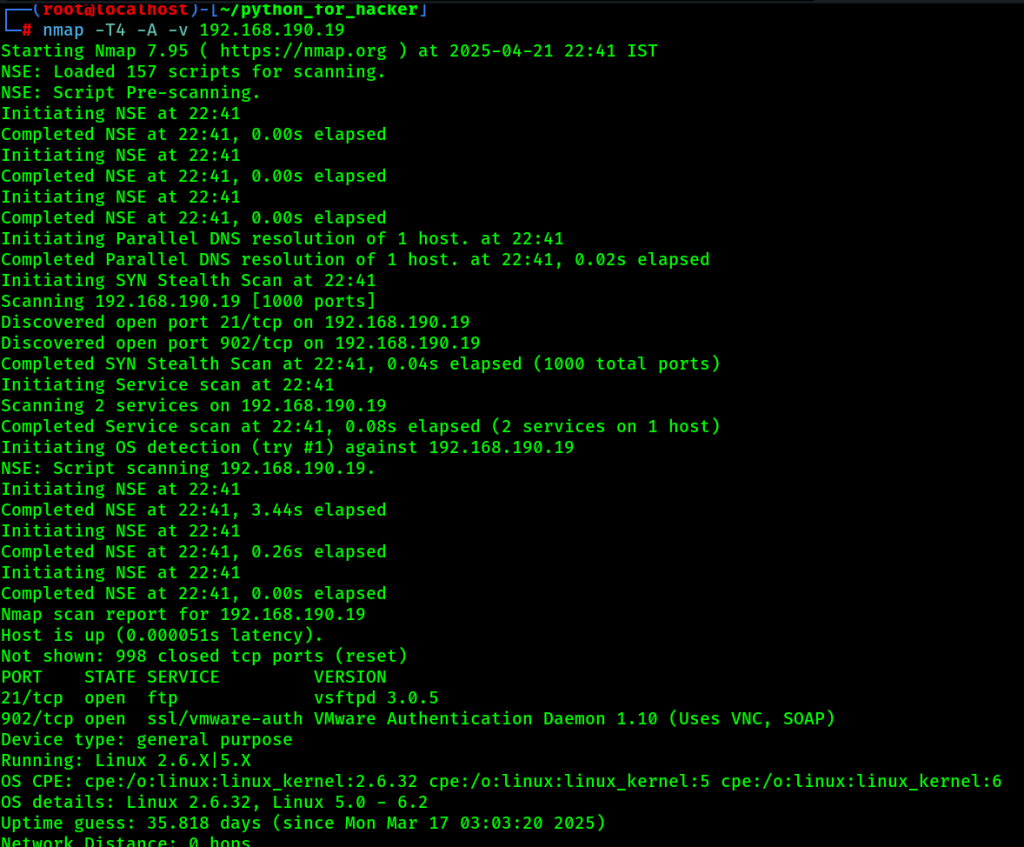
15. List Scan : -sL -v
- Command: nmap -sL -v <target>
- -sL: List targets only.
- English: Doesn’t send packets; just lists hosts.
- Hindi: Sirf target list karta hai, scan nahi karta.
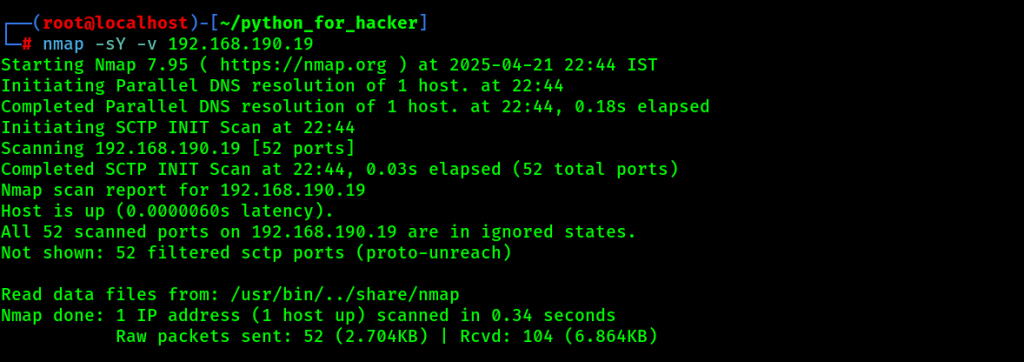
16. SCTP INIT Scan : -sY -v
- Command: nmap -sY -v <target>
- -sY: SCTP INIT scan.
- English: Sends SCTP INIT to detect open ports.
- Hindi: SCTP INIT message bhej ke ports scan karta hai.
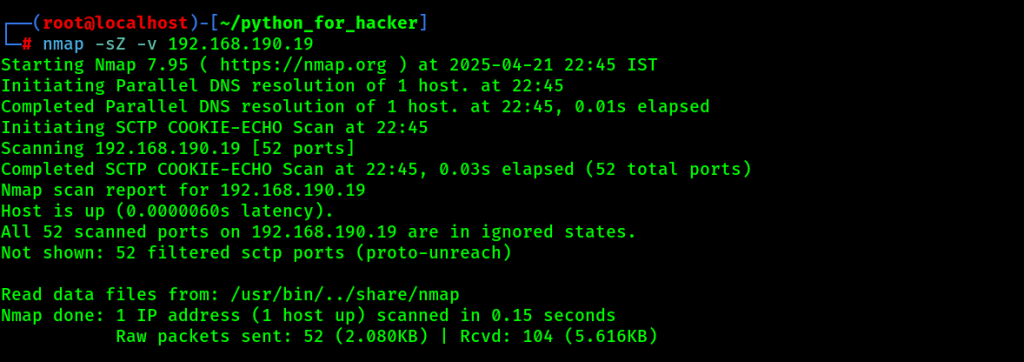
17. SCTP COOKIE ECHO Scan: -sZ -v
- Command : nmap -sZ -v <target>
- -sZ: SCTP COOKIE ECHO scan.
- English: Bypasses some filters using SCTP echo.
- Hindi: Filtering bypass karne ke liye SCTP COOKIE ECHO use karta hai.
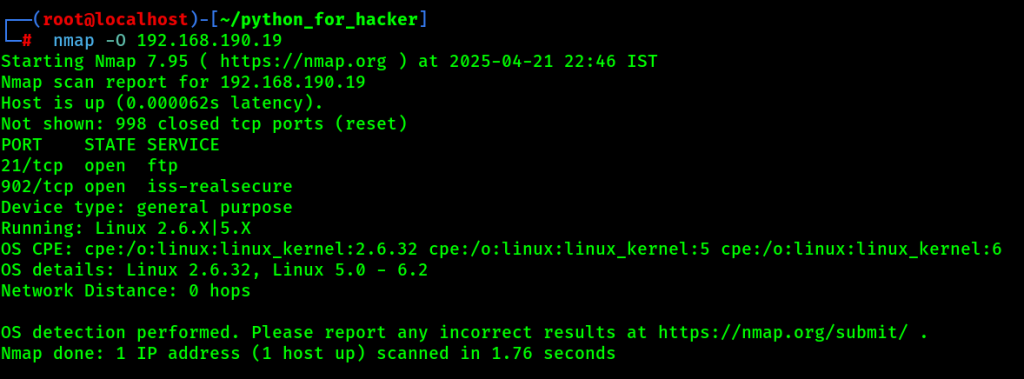
18. OS Detection : -O
- Command: nmap -O <target>
- -O: Detect operating system.
- English: Finds OS type and version.
- Hindi: System ka OS kaun sa hai yeh pata lagata hai.
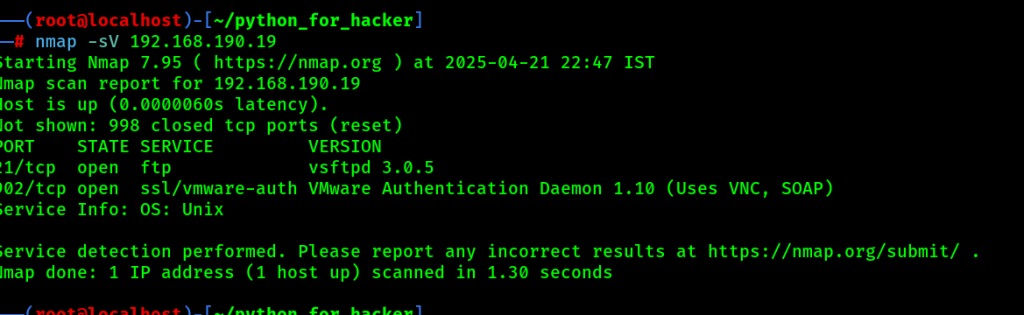
19. Service Version Detection: -sV
- Command: nmap -sV <target>
- -sV: Service detection.
- English: Finds software name & version running on ports.
- Hindi: Kaun si service aur version chal raha hai, yeh detect karta hai.
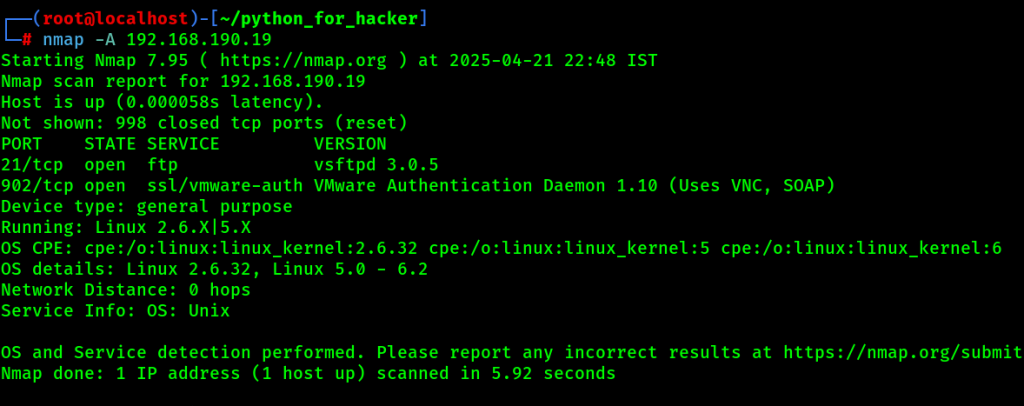
20. Aggressive Scan: -A
- Command: nmap -A <target>
- -A: Enable OS detection, version detection, script scanning, and traceroute.
- English: Powerful all-in-one scan.
- Hindi: Sab kuch ek sath scan karta hai — OS, services, traceroute, etc.
21. UDP Scan (Top 10): -sU –top-ports 10
- Command: nmap -sU –top-ports 10 <target>
- English: Scans top 10 most used UDP ports.
- Hindi: Top 10 UDP ports scan karta hai jaldi result ke liye.
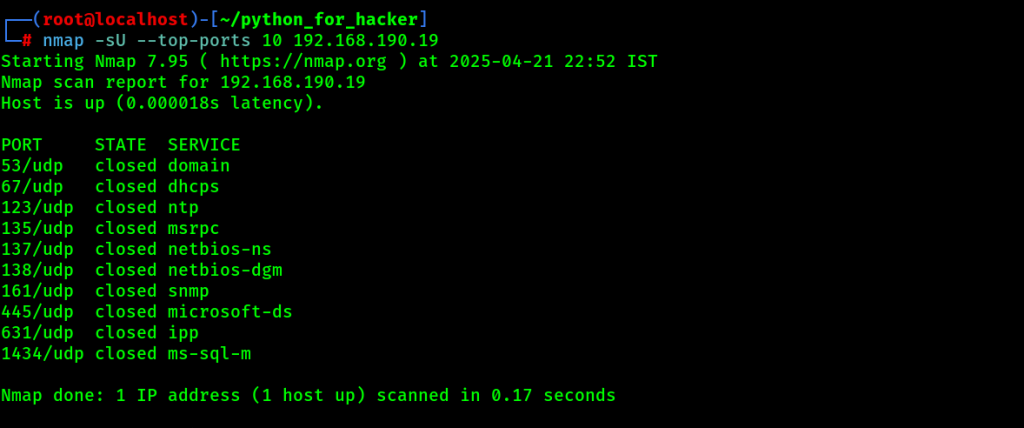
22. Top 1000 TCP Ports: –top-ports 1000
- Command: nmap –top-ports 1000 <target>
- English: Scans the most common 1000 TCP ports.
- Hindi: Sabse zyada use hone wale 1000 TCP ports scan karta hai.
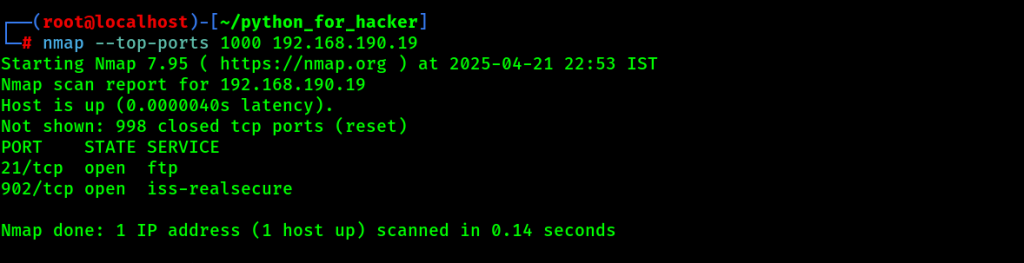
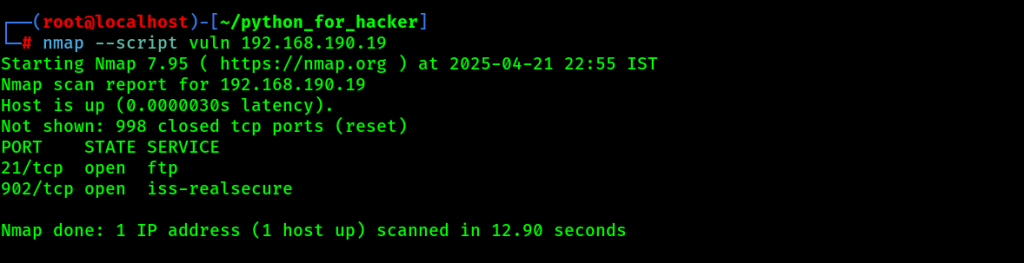
23. Vulnerability Scan: –script vuln
- Command : nmap –script vuln <target>
- English: Runs vulnerability detection scripts.
- Hindi: Target pe vulnerability scan karta hai using Nmap scripts.
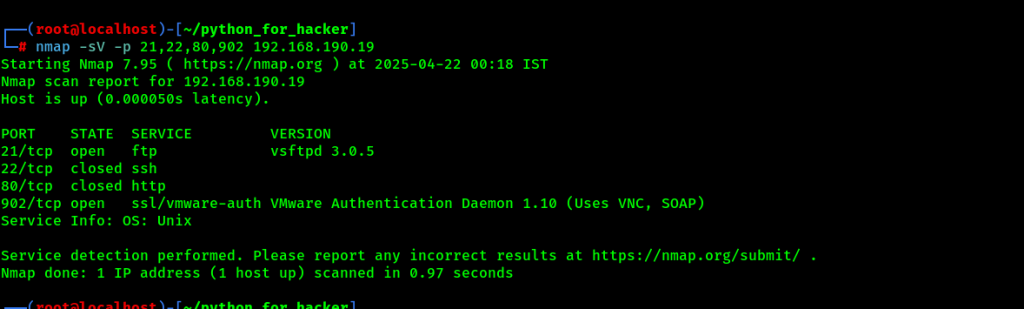
24. Service Version Scan on Specific Ports : -sV -p
- Command: nmap -sV -p 21,22,80,902 <target>
- -sV : Detect service versions running on open ports.
- -p : Scan only selected ports (here 21, 22, 80).
- English : Scan selected ports to know which services and their versions are running.
- Hindi : Sirf diye gaye ports ko scan karta hai aur batata hai ki kaunsi service kaunsa version chal raha hai.
25. Default Scripts Scan: -sC
-
Command: nmap -sC <target
> - English: Runs default set of Nmap scripts for basic service enumeration.
- Hindi: Target pe Nmap ke default scripts se basic service information gather karta hai.
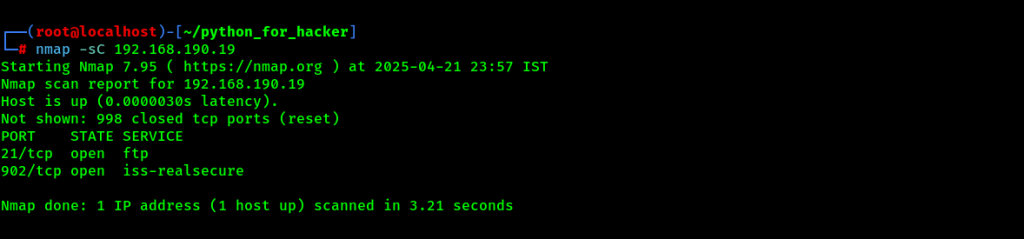
26. Full Port Scan : -p--
- Command: nmap -p- <target>
- English: Scans all 65535 ports.
- Hindi: Target ke saare 65535 ports scan karta hai, na ki sirf top 1000.
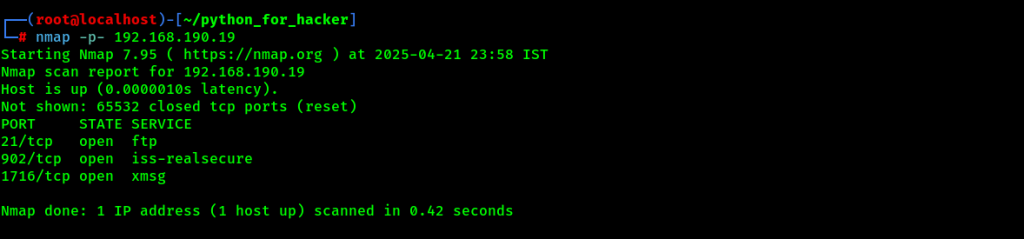
27. FTP Anonymous Access Scan : –script ftp-anon
- Command: nmap –script=ftp-anon <target>
- English: Checks if FTP allows anonymous login.
- Hindi: Check karta hai ki FTP pe bina login ke (anonymous) access mil raha hai ya nahi.
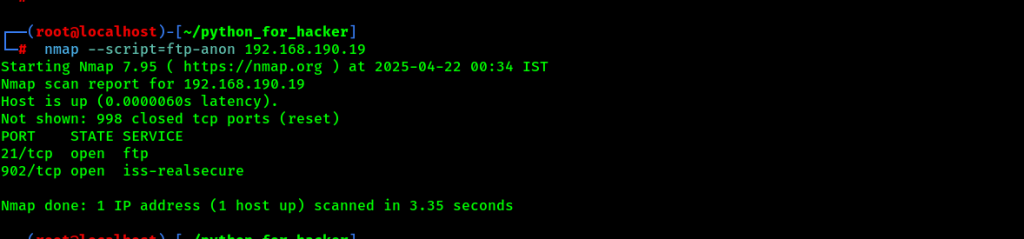
28. Multi-Script Scan: –script ftp-anon,http-title,vuln
- Command: nmap –script=ftp-anon,http-title,vuln <target>
- English: Runs multiple scripts for FTP, HTTP title, and vulnerabilities.
- Hindi: Ek saath 3 scripts chalaata hai – FTP anonymous access, website title aur vulnerability check ke liye.
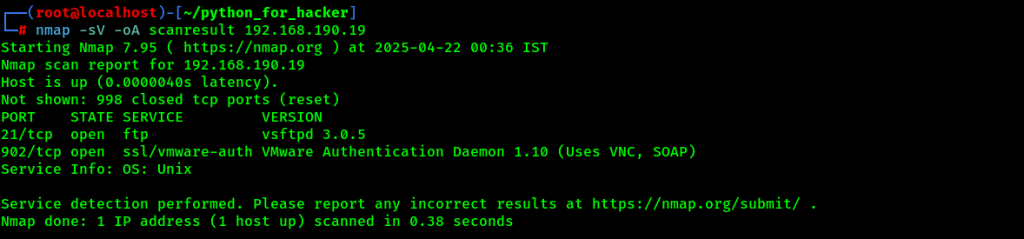
29. Service Version & Output Save : -sV -oA
- Command: nmap -sV -oA scanresult <target>
- English: Detects service versions and saves output in all formats.
- Hindi: Services ke versions detect karta hai aur output ko 3 formats me save karta hai (.nmap, .xml, .gnmap).
30. Timing Template: -T0 to -T5
- Command: nmap -T0 to -T5 <target>
- English: Controls scan speed from paranoid (T0) to insane (T5).
- Hindi: Scan ki speed control karta hai, jisme T0 bohot slow aur T5 bohot fast hota hai.
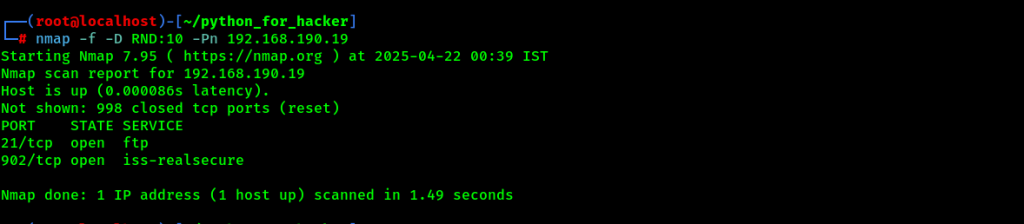
31. Stealth Scan: -f -D RND:10 -Pn
- Command: nmap -f -D RND:10 -Pn <target>
- English: Uses fragmented packets, decoys, and skips host discovery.
- Hindi: Packet ko fragment karta hai, decoys use karke attacker IP chhupata hai aur host discovery skip karta hai.
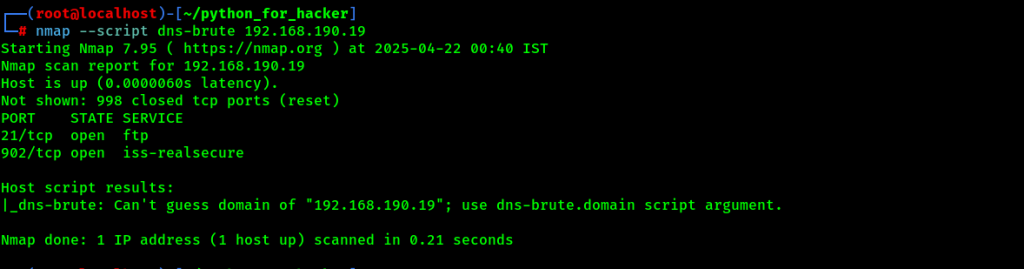
32. DNS Subdomain Brute Force: –script dns-brute
- Command: nmap –script dns-brute <target>
- English: Discovers subdomains using DNS brute-force.
- Hindi: DNS brute-force karke hidden subdomains jaise admin.domain.com dhoondta hai.
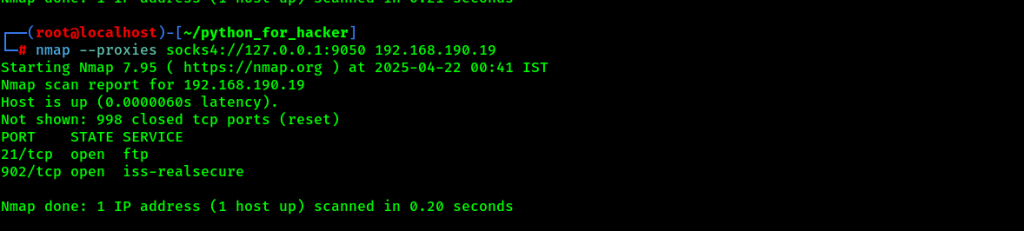
33. Scan via Proxy (TOR): –proxies socks4://127.0.0.1:9050
- Command: nmap –proxies socks4://127.0.0.1:9050 <target>
- English: Routes scan through a proxy (like TOR).
- Hindi: TOR proxy ke through scan bhejta hai taaki real IP hide rahe.
34. IPv6 Address Scan: -6
- Command: nmap -6 <target>
- English: Scans using IPv6 addressing.
- Hindi: Target ka IPv6 address use karke scan karta hai.
Conclusion:
English:
In this blog, we’ve explored some of the most commonly used Nmap commands and their practical use cases. Whether you are a beginner or an experienced ethical hacker, understanding these commands can greatly enhance your ability to perform network scans and assess vulnerabilities.
Remember, Nmap is a powerful tool for network discovery, vulnerability assessment, and security auditing. Always use it ethically and ensure you have the proper permissions before scanning any network.
Stay curious, keep learning, and don’t hesitate to experiment with Nmap to strengthen your hacking skills!
Hindi:
Is blog mein, humne kuch commonly used Nmap commands aur unke practical use cases ko explore kiya hai. Chahe aap beginner ho ya ek experienced ethical hacker, in commands ko samajhna aapki network scanning aur vulnerabilities assess karne ki ability ko bahut enhance kar sakta hai.
Yaad rakhein, Nmap ek powerful tool hai network discovery, vulnerability assessment, aur security auditing ke liye. Hamesha ise ethically use karein aur kisi bhi network ko scan karne se pehle proper permissions lein.
Curious rahiye, seekhte rahiye, aur Nmap ka use karke apne hacking skills ko mazboot banaiye!
![]()





One Comment